How IAM is becoming necessity for digital enterprise
In the post pandemic era, where enterprises are looking forward to hybrid workforce, IT Security admin face a challenging task of providing authorized access to resources. Enterprises want reliable and easy-to-use IAM tools —while ensuring that the user experience is not compromised.
An Identity and Access Management system assigns each user (human or machine), a unique digital identity and manages the rights associated with that identity. With these identities, you can give users—including employees, customers and vendors—appropriate access to specific applications in order to prevent accidental internal breaches.
Why is an IAM solution becoming a compelling need?
The pandemic has seen a humongous increase in cyber-attacks on not only businesses but also critical infrastructure. IAM has become a necessity to protect your business from cybersecurity threats and should be an IT Security priority for any company. Simply put, an IAM tool should have the following components:
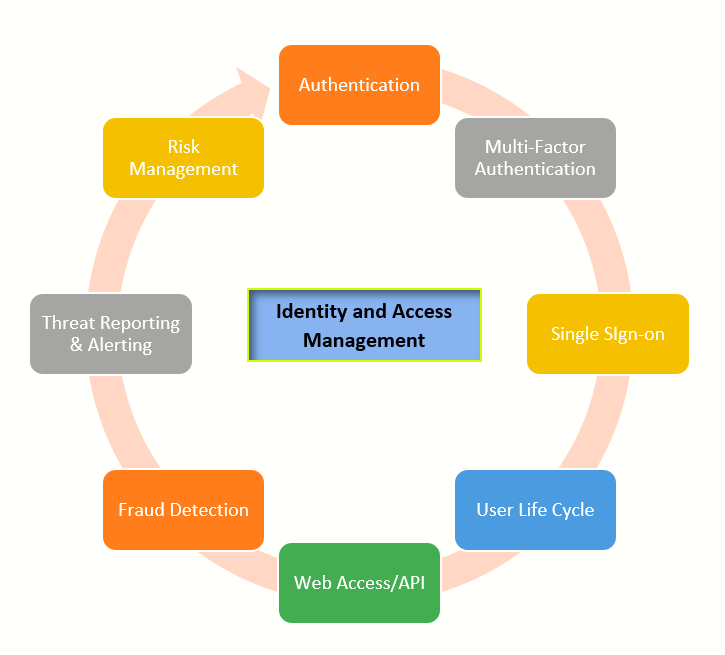
- Authentication: Ensure your users are who they say they are, without compromising their digital experience.
Authentication is one of the most fundamental functions of an IAM system. This capability requires that a user prove their identity when they want to access an app or system through a login process. Once the user provides their credentials (username/password, fingerprint scan etc.) the system uses that to verify that the user is who they claim to be and then allows the user access. According to various studies, over 80% of successful data breaches are due to weak or compromised passwords. Therefore, login security is at the core of any IAM system. By using unique next gen multi-layer Rainbow secure password and zero-trust passwordless login methods organizations can establish and enforce robust login security throughout the organization.
- Multi-factor authentication (MFA): Double-check that your users are who they say they are.
When a system or app is secured through MFA, the user needs more than one “authentication factor” to log in. Typically, this is something the user knows, such as a password or PIN, plus something the user has. This provides an extra level of security in the event that a user’s password is compromised; cybercriminals will be unable to log in without the second authentication factor. Rainbow Secure Smart MFA takes it further and provides multi-layer multi-factor defense against phishing, smishing and man in the middle attacks. While no two solutions and deployments are the same, your organization should evaluate IAM SSO tools and MFA options that solve modern cyber threats and address the challenges that your organization wants to solve.
- Single Sign-On: Provide secure one-click access to apps, anytime and anywhere.
Single sign-on is an IAM core capability that allows users to sign in to all of your applications and services via just one set of credentials, so they only have to log in once. Essentially, this means one-click access from any device for your employees and customers, reducing the need for them to manage separate accounts and passwords for each app.
- User Lifecycle: Securely manage identity and profile data at scale.
With so many user accounts to manage, an important IAM tool is to maintain the user lifecycle.
- Web/API Access: Enable secure access management for apps and APIs.
Utilizing identity attributes and other contextual data can improve security by ensuring authenticated users have access only to appropriate apps, resources and APIs.
- Fraud Detection: Detect online fraud before transactions using behavioral data. With an increasing number of transactions happening online, fraudsters are spreading their methods of defrauding businesses. You can stop them with advanced fraud detection that finds bots, account takeovers, and new account fraud. This IAM tool detects fraud behind the scenes before it happens without creating more headaches for genuine users.
- Threat Reporting and Alerting
Use artificial intelligence to defend sensitive data and business systems. geoACL and Rainbow Secure’s proprietary AI based algorithms will flag possible frauds, provide threat reports and alert the key personnel based on threat level.
- Risk Management: Detect threats and make more intelligent authentication decisions.
By integrating risk management into your authentication flows and policies, you can reduce login friction and avoid allowing bad actors to gain access by making decisions based on various signals provided by the user, network, device and more. Risk Management works by capturing characteristics of a user’s session such as location, session timings, unexpected user activity. These characteristics can include a user’s device, what network they’re signing on from and other aspects of their behavior to make those intelligent authentication decisions.
Benefits of IAM
The most obvious benefit to a robust IAM solution is enhanced security, particularly in a post-pandemic world where hybrid work has become a norm than an exception. Next gen IAM systems will enable IT administrators to control user access regardless of where employees are working from or what devices they are using.
Similarly, IAM also enables organizations to grant systems access to users outside the organization, such as partners, contractors, and vendors, without jeopardizing security. A robust IAM system also:
- Provides greater compliance by forcing organizations to explicitly define their user access policies and procedures, as required by HIPAA, Sarbanes-Oxley, and NIST guidelines. Several IAM solutions provide audit and reporting tools specifically designed for compliance audits.
- Provides proof of compliance and due diligence if an organization is breached.
- Reduces help desk workloads by eliminating requests for password resets and enabling IT administrators to automate many routine tasks.
- Drives innovation by enabling organizations to securely extend network access to a variety of on-premises and SaaS apps.
Choosing an IAM Vendor
Next-gen IAM solutions will provide comprehensive security for your organization and keep it safe from cyber threats and data breaches. Your cyber liabilities from past credential breaches will also reduce from Day 1 because of interactive graphical security.
Book a Demo with Rainbow Secure and make the right choice for your enterprise.